...
Together these 2 sets of components make up an interoperability layer. These can be seen in the diagram below. In the following section we will describe the requirement for the key requirements for the interoperability layer and explore each of these components in more details.
Key Requirements
The full requirements that the Interoperability Layer community have identified can be found here: What is an Interoperability Layer?
Here are the key is list of key requirements that are seen as beneficial for an interoperability layer:
- Provide a central point for authentication and authorization to the HIE services.
- Log, audit and monitor communication communications with the components of the HIE.
- Provide error management and transaction monitoring information to the manager administrators of the HIE.
- Provide transaction orchestration service and adapters services as well as adapter services to transform message between different message formats.
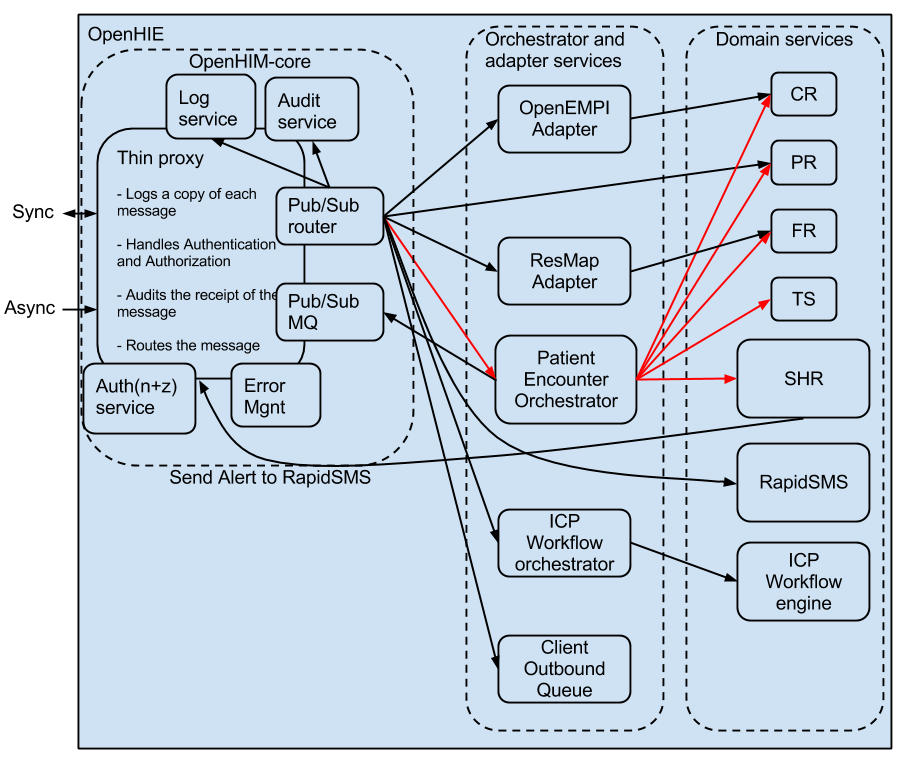
The architecture
The core (thin proxy) component
This component can be through thought of as the entry point into the HIE. In It provides some common mundane services so that other domain services don't have to implement these. This component basically just acts as a web service proxy while performing some additional functions on the incoming requests. The functions that this component should perform are as follow:
...
The interoperability layer core component contacts each one of these services when it receives a message to ensure the appropriate information is stored. It then passes the message on to the router where it is sent to the correct upstream service. The routers make use of a publish and subscribe pattern so that messages can be routed to multiple interested parties. This allows for secondary use of the messages received by the HIE. For example, encounter message could be routed to the SHR as well as a agggregation an aggregation service where they could be aggregated and submitted to an aggregate data store such as DHIS. There are 2 types of routers:
...
This set of components provides services that manipulate the request requests that are sent to them. They are often implementation specific so they will change as the use cases that the HIE supports change. Each of these components are separate, independent services that perform a specific function following the micro services architecture (http://yobriefca.se/blog/2013/04/29/micro-service-architecture/). There are 2 major types of these services:
- Orchestrators - This service type enables a business process to be executed, this normally involved involves one or more additional service being invoked to process the required transaction.
- Adapters – This service type adapts a incoming request to a form that the intended recipient of the request can understand.
These services are invoked whenever there is a need to orchestrate or adapt a certain transaction. If they are not needed the core interoperability layer component will just call the domain service directly. Designing these as independent services allows additional logic or business processes to be included in added to the HIE as the need arises. This allows the architecture to grow as the environment changes.
...
With the interoperability layer being a central component of the health information exchange there are a number of features that present themselvesbecome apparent. Some of these are positive features and other are negative features. These are listed below:
Certificate management is centralised, this allows for easier management and setup.
Domain services don’t have to all implement functionality to audit, log and authenticate message thus making them simpler.
Allows messages to be easily intercepted for secondary use which is beneficial to enable additional functions as the HIE grows.
Could be a dependency knot when other services have to join the exchange as this central component will have to be configured for each change - can could be mitigated by allowing simple pass through of web services via configuration, thus the changes are in configuration only.