- Created by Jennifer E Shivers, last modified on Nov 14, 2016
You are viewing an old version of this page. View the current version.
Compare with Current View Page History
« Previous Version 6 Next »
Step 1 - Create the ubuntu environment
The minimum hardware requirements below are suggested for a new DATIM4U implementation. Requirements will be highly dependent upon how you intend to use the DATIM Global implementation and the amount of data being stored and processed.
Quad core CPU
32 GB Memory
At least 500 GB of disk space
Ubuntu 14.04 64-bit
Internet access
- It is also recommended that the installer consider the time zone setting. The DATIM-Global system uses UTC.
Add credentials for developers or support personnel who need sudo access to the box.
certificates????
Step 2 Install software
Depending upon the need for the environment (testing, production or other need), the installer will need to determine which versions of the OpenHIM and OpenInfoman packaging to install.
2.1 Run the following command
Step 3 Configure software
3.1 nginx configuration
3.2 OpenHim Configuration
3.2.1 Setting up OpenHIM administrator alerts
It is recommended that implementers configure their system to alert systems administrators when transactions fail to exchange. Directions to configure this can be found here: OpenHIM User Guide -> Alerting and Reports -> Failure Alerting.
3.2.2 Setting up the OpenHIM Certificate
Depending upon how you obtained your certificates, the certificate files may end in .pem, .crt, .cer or .der. Also note that the administrator will need to ensure that the certificate expiration dates are managed. When the certificate expires, the administrator will need to exchange certificates again. To install certificates from a CA to replace the self-signed certificates generated during installation, perform the following steps:
We support Chrome for the installation and configuration process. The steps for 3.1 vary significantly when using different browsers as the browsers view the OpenHim as the browsers view the newly installed application as coming from an unverified source until the actual certificate is installed in the OpenHIM. Also we recommend performing Step 3.1 in an incognito mode.
3.2.2.1 - Login to OpenHim by going to http://GlobalDNSName. (where GlobalDNSName is the DNS name).
Default credentials are: root@openhim.org/openhim-password.
Note: If prompted, click on the "Advanced" (in grey) link, then "proceed..." link. The first time you login you may get the following screen:
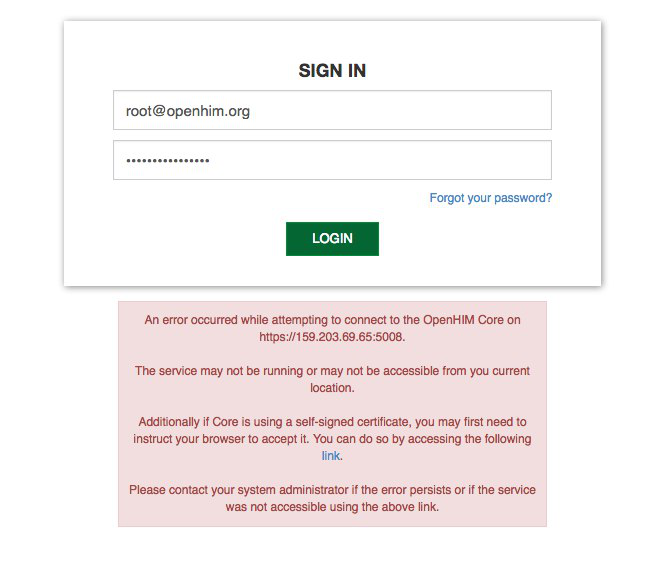
This occurs because our installation certificate is self-signed. These and other issues may occur in Safari and Firefox browsers. Follow instructions given on the error message.
3.2.2.2 Click on the "link" in the dialog, a new page will open, click on the "Advanced" (in grey) link, then "proceed..." link. Once the certificate is accepted navigate back to the log in page and sign in again.
Note: If you continue to have issues, you may ask your browser to ignore certificate errors. The steps to do this differs from operating system to operating system. You may also accomplish this by starting your browser with the '--ignore-certificate-errors --test-type’ flag. This can be done by changing chrome properties via chrome (right click) -> properties -> edit 'target' field to add the aforementioned flag.
3.2.2.3 - When logging in, a prompt will appear to change your password. Follow the on-screen directions to complete these steps.
3.2.2.4 - After successful login, on the left sidebar menu, select Certificates to display the certificates interface.
3.2.2.5 - Using the directions on screen, upload your machines's certificate and key. Please note that for "certificate expiration date", -1 does not indicate "never".
The common name should be the DNS of your server or include a wild card that includes your DNS. For example, www.DNSNAME.ohie.org. (where DNSNAME is the DNS name of your node).
Note: If your certificates were generated by the script and you are running that on a remote server then you could get the certificates your machine at yourpath location using the following command.
scp user@datim.example.com:/etc/letsencrypt/live/datim.example.com/* /yourpath .
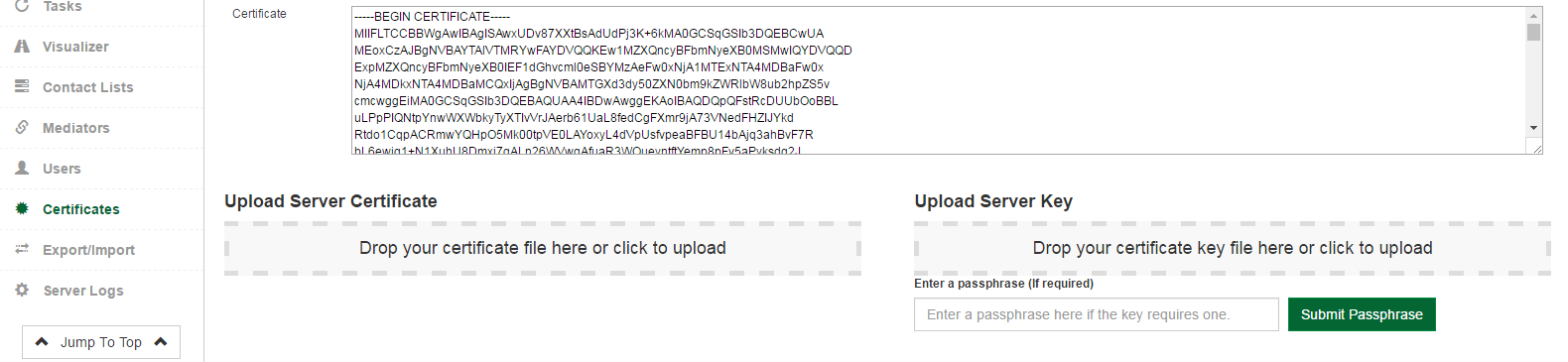
3.2.2.6 - After uploading both the certificate and the key, the OpenHim will verify that the keys match. Note that the system will notify you that the keys will not match until both files are uploaded.
3.2.2.7 - OpenHim will prompt you to re-start the system. Proceed with the re-start.
3.3 Infoman configuration
3.3.1 Create DATIM-Global document - Need help with this.
3.3.2 Create Extract documents for each OU nodes that need to work with this global instance
For each OU node that needs to work with DATIM-Global, there needs to be an extract document that contains the current OU country data that will the the source for seeding the node with their DATIM4U sites.
To create the documents use this command: curl -sL -o /dev/null --data "directory=XXOU-Extract” -X POST http://localhost:8984/CSD/createDirectory
3.3.3 Populate Extract documents
To populate each extract document, use these directions: https://wiki.ohie.org/display/resources/How+to+Configure+DATIM+Global#HowtoConfigureDATIMGlobal-ManuallypopulatingtheXXOU-Extractdocument
- No labels